Program at a Glance
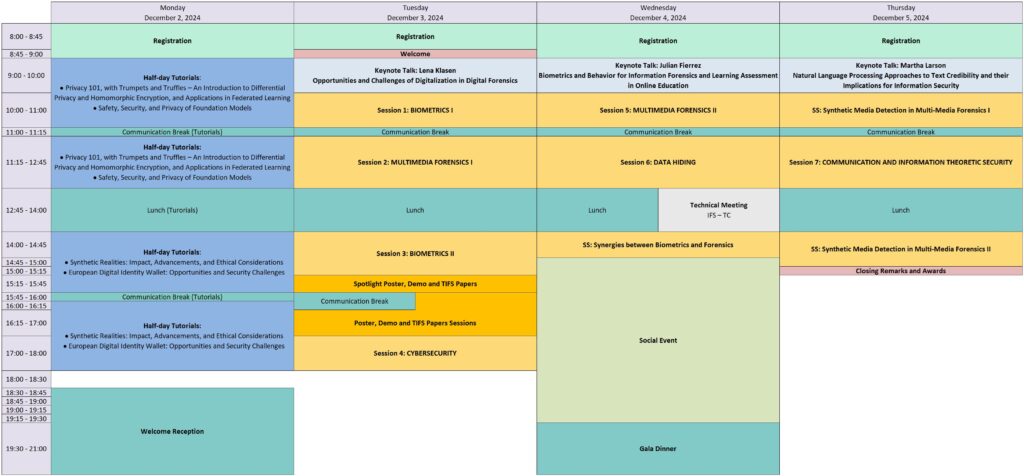
Monday, December 2, 2024
09:00 – 12:45: Half-day Tutorials
Privacy 101, with Trumpets and Truffles – An Introduction to Differential Privacy and Homomorphic Encryption, and Applications in Federated Learning by Fernando Pérez-González (University of Vigo, Spain)
Safety, Security, and Privacy of Foundation Models by Xinlei He (The Hong Kong University of Science and Technology, Guangzhou, China) and Tianshuo Cong (Tsinghua University, Beijing, China)
12:45 – 14:00: Lunch (Tutorials)
14:00 – 18:00: Half-day Tutorials
Synthetic Realities: Impact, Advancements, and Ethical Considerations by Gabriel Bertocco and Anderson Rocha (Artificial Intelligence Lab., Recod.ai, Institute of Computing, Universidade Estadual de Campinas – Unicamp, Brazil)
European Digital Identity Wallet: Opportunities and Security Challenges by Amir Sharif, Giada Sciarretta, Alessandro Tomasi (Fondazione Bruno Kessler, Trento, Italy)
18:30 – 21:00: Welcome Reception
Tuesday, December 3, 2024
08:45 – 09:00: Welcome
09:00 – 10:00: Keynote Talk
Opportunities and Challenges of Digitalization in Digital Forensics by Lena Klasén, Director of Research at the Department of National Operations of Sweden, and Ajd. Professor Digital Forensics, Computer Vision Laboratory, Linköping University, Sweden
10:00 – 11:00: Oral Session 1 – Biometrics I (Chair: Patrizio Campisi)
Explainable Presentation Attack Detection of Digital Fingerprints by Augustin Diers (GREYC), Christophe Rosenberger (ENSICAEN)
Effectiveness of learning-based image codecs on fingerprint storage by Daniele Mari (Università degli studi di Padova), Saverio Cavasin (Università di Padova), Simone Milani (University of Padova), Mauro Conti (University of Padua)
TempCharBERT: Keystroke Dynamics for Continuous Access Control Based on Pre-trained Language Models by Matheus Simão Caixeta, Fabiano oliveira costa prado (unesp), Omar Abdul Wahab (Polytechnique Montréal), Anderson R Avila (INRS-EMT)
Synthetic Ethnicity Alteration for Diversifying Face Datasets – Investigating Recognition and Quality by Praveen Kumar Chandaliya (Sardar Vallabhbhai National Institute of Technology ), Kiran Raja (NTNU), Haoyu Zhang (NTNU), Raghavendra Ramachandra (NTNU, Norway), Christoph Busch (NTNU)
11:00 – 11:15: Communication Break
11:15 – 12:45: Oral Session 2 – Multimedia Forensics I (Chair: Iuliia Tkachenko)
Assessing shadows and reflections consistency in AI-generated images by Massimo Iuliani (Amped Software), Stefano Bianchi (Amped Software), Andrea Paghera (European Forensic Institute), Marco Fontani (Amped Software), Martino Jerian (Amped Software)
Assessing the Viability of Synthetic Physical Copy Detection Patterns on Different Imaging Systems by Roman Chaban (University of Geneva), Brian Pulfer (University of Geneva), Slava Voloshynovskiy (University of Geneva)
A Taxonomy of Miscompressions: Preparing Image Forensics for Neural Compression by Nora Hofer (University of Innsbruck), Rainer Böhme (University of Innsbruck)
Spectrogram-Based Detection of Auto-Tuned Vocals in Music Recordings by Mahyar Gohari (University of Brescia), Paolo Bestagini (Politecnico di Milano), Sergio Benini (University of Brescia), Nicola Adami (University of Brescia)
PLUS Temporal Image Forensics Dataset by Robert Jöchl (University of Salzburg), Andreas Uhl (University of Salzburg)
Interactive Event Sifting using Bayesian Graph Neural Networks by José Nascimento (Unicamp), Nathan Jacobs (Washington University in St. Louis), Anderson Rocha (UNICAMP)
12:45 – 14:00: Lunch
14:00 – 15:15: Oral Session 3 – Biometrics II (Chair: Mathias Ibsen)
Fixed-length Dense Descriptor for Efficient Fingerprint Matching by Zhiyu Pan (Tsinghua University), Yongjie Duan (Tsinghua University, China), Jianjiang Feng (Tsinghua University), Jie Zhou (Tsinghua University)
Strengthened Fuzzy Extractors using Turbo-codes: Case Study on Finger Vein Authentication by Enrique Argones Rua (KU Leuven), Emanuele Maiorana (Roma Tre University), Patrizio Campisi (Roma Tre University)
Ternary Neural Networks for Gait Identification in Wearable Devices by Giacomo Agnetti (Politecnico di Torino), Andrea Migliorati (Politecnico di Torino), Daniele Mari (Università degli studi di Padova), Tiziano Bianchi (Politecnico di Torino), Simone Milani (University of Padova), Enrico Magli (POLITO)
Vision through distortions: Atmospheric Turbulence- and Clothing-invariant long-range recognition by Gabriel Capiteli Bertocco (University of Campinas), Fernanda Andaló (University of Campinas), Terrance E Boult (University of Colorado Colorado Springs), Anderson Rocha (University of Campinas)
MONOT: High-Quality Privacy-compliant Morphed Synthetic Images for Everyone by Guido Borghi (University of Modena and Reggio Emilia), Nicolò Di Domenico (University of Bologna), Matteo Ferrara (University of Bologna), Annalisa Franco (University of Bologna), Uzma Latif (Univeristy of Bologna, Italy.), Davide Maltoni (University of Bologna)
15:15 – 15:45: Spotlight Poster, Demo and TIFS Papers (Chair: Roberto Caldelli)
15:45 – 16:15: Communication Break
15:45 – 17:00: Poster, Demo and TIFS Papers Sessions (Chair: Roberto Caldelli)
Poster Session
Take It Easy: Label-Adaptive Self-Rationalization for Fact Verification and Explanation Generation by Jing Yang (University of Campinas), Anderson Rocha (University of Campinas)
Privacy Preserving Protest Dynamics by Cohen G Archbold (University of Kentucky), Usman Hassan (University of Kentucky), Nazmus Sakib (University of Kentucky), Sen-ching Samoson Cheung (Mialab), Abdullah Al Zubaer Imran (University of Kentucky)
When does gradient estimation improve black-box adversarial attacks? by Enoal Gesny (Inria), Eva Giboulot (Inria Rennes), Teddy Furon (Inria)
Privacy-aware Berrut Approximated Coded Computing applied to Federated Learning by Xavier Martínez-Luaña (GRADIANT), Manuel Fernández Veiga (University of Vigo), Rebeca Díaz-Redondo (Universidade de Vigo)
Demo Session
MedTech Chain: Decentralised, Secure and Privacy-preserving Platform for Medical Device Data Research by Alin Petru-Rosu (TU Delft), Tamara Tataru (TU Delft ), Jegor Zelenjak (TU Delft), Roland Kromes (TU Delft), Zekeriya Erkin (TU Delft)
MedGuard: Securing Medical iot with compiler polymorphism by Dimitris Santorinaios (Zortenet), Akis Kourtis (Zortenet), George Oikonomakis (Zortenet)
Unmasking the Unseen: CryptojackingTrap, the Most Resilient Evasion-Proof Cryptojacking Malware Detection Algorithm by Atefeh Zareh Chahoki (University of Trento), Hamid Reza Shahriari (Amirkabir University of Technology), Marco Roveri (University of Trento)
TIFS Papers
CryptojackingTrap: An Evasion Resilient Nature-Inspired Algorithm to Detect Cryptojacking Malware by Atefeh Zareh Chahoki (University of Trento), Hamid Reza Shahriari (Amirkabir University of Technology), and Marco Roveri (University of Trento)
Adaptive Differentially Quantized Subspace Perturbation (ADQSP): A Unified Framework for Privacy-Preserving Distributed Average Consensus by Qiongxiu Li (Tsinghua University), Jaron Skovsted Gundersen (Aalborg University), Milan Lopuhaä-Zwakenberg (University of Twente) , Richard Heusdens (Netherlands Defence Academy)
Fully Symmetrical Obfuscated Interconnection and Weak-PUF-Assisted Challenge Obfuscation Strong PUFs Against Machine-Learning Modeling Attacks by Chongyao Xu (University of Macau); Litao Zhang (University of Macau); Pui-In Mak (Universidade de Lisboa); Rui P. Martins (University of Macau) Man-Kay Law (University of Macau)
17:00 – 18:00: Oral Session 4 – Cybersecurity (Chair: Rainer Böhme)
Smart Contract Kill Switch for Security in a Private Blockchain-based Software Transaction System by Soonhong Kwon (Sejong University), Wooyoung Son (Sejong University), Jong-Hyouk Lee (Sejong University)
GUARD: Graph-based Unknown Attack Recognition and Detection by Shane R Dirksen (UC Santa Barbara), John Korah (Cal Poly Pomona)
Efficient Audio Deepfake Detection using WavLM with Early Exiting by Arthur S Pimentel (Institut National de la Recherche Scientifique (INRS)), Yi Zhu (Institut national de la recherche scientifique (INRS)), Heitor R Guimarães (Institut National de la Recherche Scientifique), Tiago H Falk (INRS-EMT)
Collective Threshold Multiparty Private Set Intersection Protocols for Cyber Threat Intelligence by Chelsea Guan (Delft University of Technology), Jorrit van Assen (Delft University of Technology), Zekeriya Erkin (TU Delft)
Wednesday, December 4, 2024
09:00 – 10:00: Keynote Talk
Biometrics and Behavior for Information Forensics and Learning Assessment in Online Education by Julian Fierrez, Full Professor at Universidad Politecnica de Madrid, Madrid, Spain
10:00 – 11:00: Oral Session 5 – Multimedia Forensics II (Chair: Bin Li)
Now ForReal: Towards Practical Forensic Room Identification with Real-World Audio Data by Denise Moussa (Friedrich-Alexander-University Erlangen-Nuremberg/Federal Criminal Police Office of Germany), Leon Huber (Friedrich-Alexander University Erlangen-Nuremberg), Germans Hirsch (Friedrich-Alexander University Erlangen-Nuremberg), Christian Riess (Friedrich-Alexander University Erlangen-Nuremberg)
Tiny autoencoders are effective few-shot generative model detectors by Luca Bindini (University of Florence), Giulia Bertazzini (University of Florence), Daniele Baracchi (Università degli Studi di Firenze), Dasara Shullani (University of Florence), Paolo Frasconi (University of Florence), Alessandro Piva (Department of Information Engineering – University of Florence)
Beyond the Brush: Fully-automated Crafting of Realistic Inpainted Images by Giulia Bertazzini (University of Florence), Chiara Albisani (University of Florence), Daniele Baracchi (Università degli Studi di Firenze), Dasara Shullani (University of Florence), Alessandro Piva (Department of Information Engineering – University of Florence)
SWIFT: Semantic Watermarking for mage Forgery Thwarting by Gautier Evennou (IRISA/IMATAG), Vivien Chappelier (IMATAG), Ewa Kijak (IRISA), Teddy Furon (Inria)
11:00 – 11:15: Communication Break
11:15 – 12:45: Oral Session 6 – Data Hiding (Chair: Eva Giboulot)
Transferable Watermarking to Self-supervised Pre-trained Graph Encoders by Trigger Embeddings by Hanzhou Wu (Shanghai University)
Steganalysis in Directional JPEG Images by Benedikt Lorch (Universität Innsbruck), Rainer Böhme (University of Innsbruck)
Evaluation of Security of ML-based Watermarking: Copy and Removal Attacks by Vitaliy Kinakh (University of Geneva), Brian Pulfer (University of Geneva), Yury Belousov (University of Geneva), Pierre Fernandez (Inria), Teddy Furon (Inria), Slava Voloshynovskiy (University of Geneva)
Errorless Robust JPEG Steganography for Pixel Images by Jan Butora (CNRS), Patrick Bas (CNRS), Etienne Levecque (CNRS)
How to Form Bags in Batch Steganography by Eli Dworetzky (Binghamton University), Jessica Fridrich (“SUNY, Binghamton”)
Kerckhoffs in Prison: A Study of the Steganalyst’s Knowledge by Martin Beneš (Universität Innsbruck), Rainer Böhme (University of Innsbruck)
12:45 – 14:00: Lunch
14:00 – 14:45: Special Session – Synergies between Biometrics and Forensics (Chair: Marta Gomez-Barrero)
AgeDiff: Latent Diffusion-based Face Age Editing with Dual Cross-Attention by Marcel Grimmer (NTNU), Christoph Busch (Norwegian University of Science and Technology)
SynChildFace: Fine-tuning Face Recognition for Children with Synthetic Data by Franck V. Souop Kouam (Hochschule Darmstadt), Christian Rathgeb (Hochschule Darmstadt), Mathias Ibsen (Hochschule Darmstadt), Christoph Busch (Hochschule Darmstadt)
Combined CNN and ViT features off-the-shelf: Another astounding baseline for recognition by Fernando Alonso-Fernandez (Halmstad University), Kevin Hernandez-Diaz (Halmstad University), Prayag Tiwari (Halmstad University), Josef Bigun (Halmstad University, Sweden)
Thursday, December 5, 2024
09:00 – 10:00: Keynote Talk
Natural Language Processing Approaches to Text Credibility and their Implications for Information Security by Martha Larson, Professor of Multimedia Information Technology at Radboud University, Nijmegen, Netherlands
10:00 – 11:00: Special Session – Synthetic Media Detection in Multi-Media Forensics I (Chairs: Stefano Tubaro and Paolo Bestagini)
Explainable Artifacts for Synthetic Western Blot Source Attribution by João Phillipe Cardenuto (Unicamp), Sara Mandelli (Politecnico di Milano), Daniel Moreira (Loyola University Chicago), Paolo Bestagini (Politecnico di Milano), Edward Delp (Purdue University), Anderson Rocha (UNICAMP)
On the use of mixup augmentation for synthetic image attribution in the wild by Jun Wang (University of Siena), Benedetta Tondi (University of Siena), Mauro Barn (Universty of Siena)
When Synthetic Traces Hide Real Content: Analysis of Stable Diffusion Image Laundering by Sara Mandelli (Politecnico di Milano), Paolo Bestagini (Politecnico di Milano), Stefano Tubaro (Politecnico di Milano, Italy)
Localization of Synthetic Manipulations in Western Blot Images by Anmol Manjunath (Politecnico di Milano), Viola Negroni (Politecnico di Milano), Sara Mandelli (Politecnico di Milano), Daniel Moreira (Loyola University Chicago), Paolo Bestagini (Politecnico di Milano)
11:00 – 11:15: Communication Break
11:15 – 12:45: Oral Session 7 – Communication and Information Theoretic Security (Chair: Fernando Pérez-Gonzàlez)
Randomized Distributed Function Computation with Semantic Communications: Applications to Privacy by Onur Günlü (Linköping University)
Provable Performance Guarantees of Copy Detection Patterns by Joakim Tutt (University of Geneva), Slava Voloshynovskiy (University of Geneva)
PUF Authentication for a Modular Coding Scheme by Johannes Voichtleitner (Technical University of Munich), Christoph Frisch (Technical University of Munich), Ullrich Mönich (Technical University of Munich), Michael Pehl (Technical University of Munich), Luis Torres-Figueroa (Technische Universität München), Moritz Wiese (Technical University of Munich)
Detecting 5G Narrowband Jammers with CNN, k-nearest Neighbors, and Support Vector Machines by Matteo Varotto (Hochschule Darmstadt), Florian Heinrichs (Hochschule Darmstadt), Timo Schuerg (Hochschule Darmstadt), Stefano Tomasin (University of Padova), Stefan Valentin (Darmstadt University of Applied Sciences)
DPGEM: Differentially Private Generative Model with Exponential Mechanism by Usman Hassan (University of Kentucky), Jiangyue Zhu (University of Kentucky), Dongjie Chen (University of California, Davis), Sen-Ching Samson Cheung (University of Kentucky)
Vulnerabilities in Machine Learning-Based Voice Disorder Detection Systems by Gianpaolo Perelli (University of Cagliari), Andrea Panzino (University of Cagliari), Roberto Casula (University of Cagliari), Marco Micheletto (University of Cagliari), Giulia Orrù (University of Cagliari), Gian Luca Marcialis (University of Cagliari)
12:45 – 14:00: Lunch
14:00 – 15:00: Special Session 3 – Synthetic Media Detection in Multi-Media Forensics II (Chairs: Stefano Tubaro and Paolo Bestagini)
Spotting fully-synthetic facial images via local camera surface frames by Andrea Ciamarra (University of Florence and Universitas Mercatorum), Roberto Caldelli (CNIT, National Interuniversity Consortium for Telecommunications and Universitas Mercatorum), Alberto Del Bimbo (University of Florence)
TGIF: Text-Guided Inpainting Forgery Dataset by Hannes Mareen (Ghent University), Dimitrios Karageorgiou (Information Technologies Institute – Centre for Research and Technology Hellas), Glenn Van Wallendael (Ghent University), Peter Lambert (Ghent University), Symeon Papadopoulos (Information Technologies Institute – Centre for Research and Technology Hellas
Exploring the Adversarial Robustness of CLIP for AI-generated Image Detection by Vincenzo De Rosa (Università degli Studi di Napoli Federico II), Fabrizio Guillaro (University of Naples Federico II), GIovanni Poggi (University Federico II of Naples), Davide Cozzolino (University Federico II of Naples), Luisa Verdoliva (University Federico II of Naples)
Attribution of Diffusion Based Deepfake Speech Generators by Kratika Bhagtani (Purdue University), Amit Kumar Singh Yadav (Purdue University), Paolo Bestagini (Politecnico di Milano), Edward Delp (Purdue University)
15:00 – 15:15: Closing Remarks and Awards